Tool: SSSD Extract
Aug 20, 2023Red TeamLinux Post Exploitation Share on:
Tool Link: https://github.com/z-r0crypt/SSSD-extract
Using this bash script it is possible to extract Active Directory accounts hashes when credential caching is enabled in SSSD.
$ zsh sssd-extract.sh [$FolderPath]
Without input arguments it takes the SSSD default path /var/lib/sss/db/ but you can use a different one.
If tdbdump is not installed it just lists the ldb files which contain the hashes, you can install it apt install tdb-tools or exfiltrate these files:
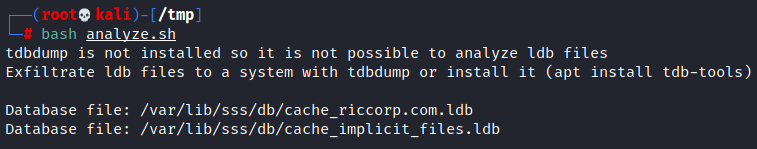
In a system with tdbdump installed the script will:
- Extracts cached accounts and hashes, dumping the results to the file
hashes.txt. The hashes can then be cracked using Hashcat or John the Ripper:
john hashes.txt --format=sha512crypt
- Extract all the AD groups, Users and Machine accounts cached in the ldb file and save it to
domain.txt
*Note: Better approach would be to copy the ldb file to you attacking machine and run the script there.
Credit
- ricardojoserf/SSSD-creds